The explosion of modern applications such as Artificial Intelligence, Machine Learning and deep learning is changing the very nature of computing and transforming businesses. These applications have opened myriad ways for companies to improve their business development processes, operations, security and provide better customer experiences. To support these applications, platforms are being designed to utilize SoCs that can process large data sets in cloud data centers, have specialized processing power to service the use cases, create customized solutions, and scale this market. The market size of AI was valued at $65.48 billion in 2020, and is projected to reach $1,581.70 billion by 2030, growing at a CAGR of 38.0% from 2021 to 2030, according to a recent report by Allied Market Research.
With this exponential growth comes rising concerns about the security on these platforms running mission-critical applications in emerging markets such as healthcare, automotive, and data analytics. Security is one of the major factors that is contributing towards the complexity as well as cost of development and maintenance of these systems. In fact, per the 2022 report published by IBM Security, the global average total cost of a data breach increased to USD 4.35 million in 2022 and has been the highest in history. What’s even more concerning is that it took an average of 207 days to identify the breach and 70 days to contain the breach.
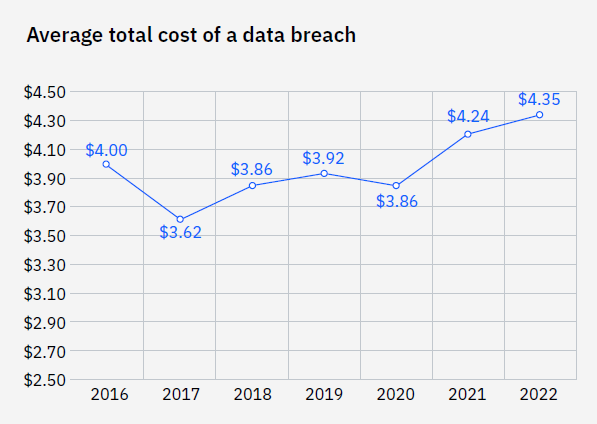
In addition to the cost, the complexity of threats that can breach these platforms by malicious actors has been increasing significantly over the past decade and it needs to be addressed with concrete security measures at the hardware, software, and protocol level on platform SoCs.
Security Threats Plaguing Cloud-Centric SoCs
The challenge for chipmakers is not only to develop high performance SoCs for cloud applications, but also to have features that can counter the sophistication of the threat vectors to secure confidential and sensitive assets on the platforms. The big question companies now ask is how much security is enough and, even if a device starts out with its security intact, will it remain secure throughout its lifetime.
This became evident with recently discovered vulnerabilities: Meltdown, Spectre, and Foreshadow which were based on speculative execution and branch prediction. Through such incidents, we have discovered how attackers use sophisticated approaches to breach a system where the threat vectors range from intrusion attacks using sniffing devices, side-channel attacks where the information during code execution is exploited to alter the device behavior, and availability-related threats, including Denial-of-Service (DoS) attacks against systems.
As these attacks become more sophisticated, next generation interconnect standards such as Compute Express Link (CXL) are also continuously adapting to protect against these threats by defining better security protocols to provide data confidentiality, integrity, and data encryption (IDE) mechanisms transiting a CXL link.
In this blog, we identify a range of the security threats that high-speed SoC devices are vulnerable to and explain how they can be countered with some of the multi-faceted cryptographic techniques defined in the CXL 2.0 specification.
CXL IDE features
Considering the modern threat vectors, the CXL Consortium, in close collaboration with other industry-standard bodies such as PCI-SIG and Distributed Management Task Force (DMTF), has incorporated the Integrity and Data Encryption (IDE) features in the CXL 2.0 specification. IDE techniques provide end-to-end protection starting from the lowest hardware levels of System on Chips (SoCs) and continue to maintain data security through the communication interface and protocols for all three CXL protocols: CXL.memory, CXL.cache and CXL.io.
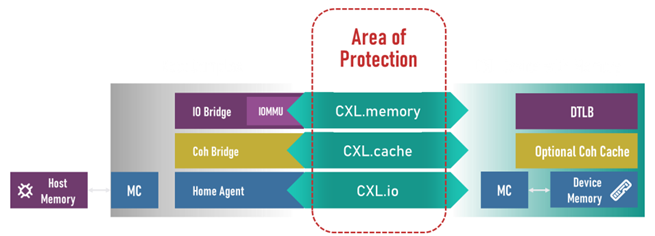
Additionally, PCRC of the packet is appended to the end of the aggregated FLIT plaintext content, encrypted, and included in the MAC computation. When implemented on all CXL devices in the path between the host and Endpoints or between Endpoints, including intermediate devices such as switches, these measures offer robustness against hard and soft faults that can be introduced by bad actors through malicious techniques such as side-channel and snooping attacks.
In addition to these techniques, two ECNs were introduced to the CXL 2.0 specification for authentication and key management:
-
Component Measurement and Authentication (CMA) defines how Security Protocol and Data Mode (SPDM) by DMTF standard is applied to CXL devices/systems.
-
Data Object Exchange (DOE) supports Data Object transport between CXL interconnects.
These measures ensure functions like authentication, attestation, measurement, identification, and key exchange, are all running in a trusted execution environment to form a Trusted Computing Base (TCB).
Error Handling
CXL IDE is designed to prevent access to user data, device secrets and keys when the device fails the integrity checks. Upon detection of a CXL.cache or CXL.mem IDE error, the integrity error is logged into CXL error reporting registers, all subsequent buffered traffic is dropped, and the device notifies the error using protocol signaling methods to the host.
Latency Considerations
While security is an essential requirement, system designers must also consider the performance needs of their systems when enabling IDE which, depending on the specific IDE chosen, can introduce additional latency. Protocol FLITs that have IDE enabled support two separate modes of operation:
-
Containment Mode where the data is released for further processing only after the integrity check passes. This mode impacts both latency and bandwidth. The bandwidth impact comes from the fact that integrity value is sent quite frequently.
-
Skid Mode where the data is released for further processing without waiting for the integrity value to be received and checked. This mode allows for less frequent transmission of the integrity value. Skid mode allows for near zero latency and very low bandwidth overhead.
Conclusion
Security is essential on high-performance interconnects and CXL helps to protect private and sensitive user information transmitted on the links. CXL IDE features provide confidentiality, integrity and replay protection for CXL.cache and CXL.mem protocol FLITs and for CXL.io TLPs. Thoughtful system considerations such as bandwidth and latency requirements need to be considered when choosing the right IDE mode for optimal system operation. These CXL security measures apply to a wide variety of use models, offer broad interoperability, and align with industry best practices.
References
-
PCI-SIG: PCIe IDE ECN
-
CXL 2.0: IDE for CXL.cache, CXL.mem protocols. CXL.io protocol refers to PCIe IDE ECN.
Compute Express Link and CXL are trademarks of the CXL Consortium. All other trademarks are the property of their respective owners.
